Harnessing GitHub for Open-Source Intelligence (OSINT)
- Jenny S.

- Jun 22
- 3 min read
Updated: 22 June 2025
When most people think of GitHub, they imagine a hub for developers sharing and collaborating on code. But for OSINT professionals, GitHub is more than just a code repository—it's a powerful and often overlooked source of intelligence. From threat actor behaviors to leaked credentials and exploit development, GitHub holds valuable insights for those who know how to search.
Why GitHub Is an OSINT Goldmine
GitHub hosts millions of public repositories, and within them lie breadcrumbs of useful intelligence. Threat actors sometimes use GitHub to share malware, publish proof-of-concept (PoC) exploits, or collaborate on tools. Others might accidentally upload sensitive information like API keys, passwords, or internal documents. Even the commit history, issues, forks, and contributors can tell a story about a person, project, or organization.
What to Look For on GitHub
Proof-of-Concept Exploits: PoCs for newly discovered vulnerabilities are often uploaded to GitHub within days (or hours) of disclosure. Monitoring these can provide early warning of new attack vectors.
Leaked Credentials: Users occasionally commit sensitive information by mistake. These secrets can be discovered through targeted searches or automated tools.
Threat Actor Activity: Some advanced persistent threat (APT) groups or hacktivists host their tooling on GitHub—sometimes under aliases, sometimes openly.
Project Metadata: Contributors, timestamps, commit messages, and issue discussions can provide useful context about a project’s purpose and the people involved.
How to Use GitHub for OSINT
There are several ways to gather intelligence from GitHub:
GitHub Dorking: Use advanced search operators to find specific types of data (e.g., password language:Python or extension:xlsx site:github.com).
APIs and Automation: Use the GitHub REST API or GraphQL API to automate searches, gather user or repo metadata, and monitor changes over time.
PyGitHub and Scrapers: Python libraries and custom scrapers can extract and structure data for analysis.
Alerting: Tools like GitHub's own "security advisories" or third-party monitoring platforms can notify you when repositories are created or updated with relevant content.
Useful GitHub-Based OSINT Tools:
GitLeaks: Scans Git repositories for secrets and credentials. Great for identifying accidental leaks in public or private repos. (GitLeaks Repo)
TruffleHog: Searches through Git repositories for high-entropy strings and secrets using regex and entropy detection. (TruffleHog Repo)
Repo-supervisor: A simple tool that runs as a CI job and checks for sensitive information in code before it's committed. (Repo-supervisor Repo)
People-Focused OSINT Tools Available on GitHub
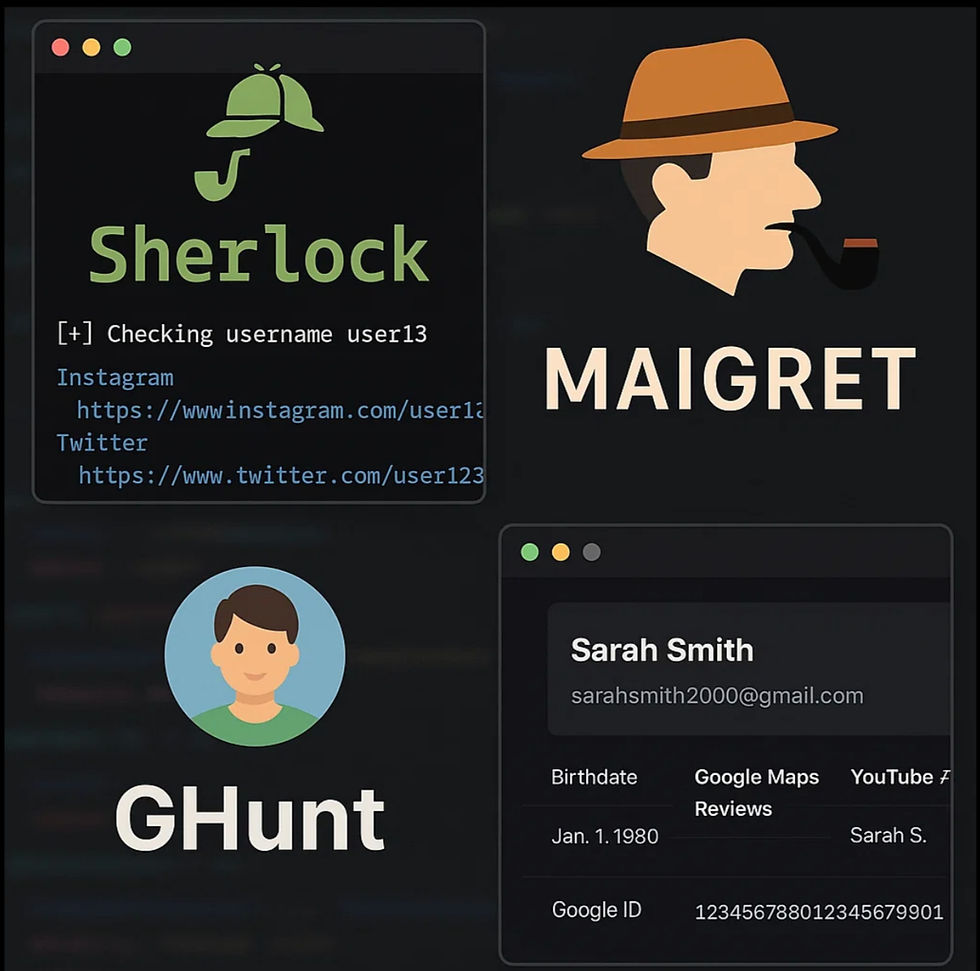
Sherlock: Finds usernames across dozens of social media platforms. Just input a name or alias, and Sherlock will identify which platforms that username exists on. It's an excellent starting point for attribution. (Sherlock Repo)
Maigret: Similar to Sherlock, but with a broader scope. Maigret can create full profiles of users by scanning hundreds of sites, and it often returns more detailed metadata. (Maigret Repo)
GHunt: Focuses on investigating Gmail addresses, revealing possible account associations, YouTube channels, calendar links, and more. GHunt is especially useful for deep-diving into online footprints. (GHunt Repo)
Ethical and Legal Considerations
Just because data is public doesn't mean it should be exploited irresponsibly. Be mindful of platform terms of service and privacy laws when scraping or storing GitHub data. Avoid targeting individuals without cause, and never use discovered credentials to access unauthorized systems.
Case Study: Detecting Leaked AWS Keys
In one investigation, a team monitoring for misconfigured cloud infrastructure found a GitHub repo where a junior developer had accidentally committed AWS access keys. Within minutes of the commit, bots had already used the keys to spin up crypto miners, costing the company thousands in cloud fees. This real-world scenario underscores the value of proactive GitHub OSINT monitoring.
Conclusion
GitHub is more than a development tool—it's a dynamic, high-value data source for open-source intelligence practitioners. With the right tools, search strategies, and ethical practices, investigators can uncover everything from emerging exploits to human behaviors. As threat a
ctors evolve, so too must the sources we monitor. GitHub is one worth watching.




Comments